3 Common Office 365 Attacks

Office 365 is a hotspot for data. Within the office suite, Microsoft offers email, collaboration, file storage, and productivity applications that include Sharepoint and Onedrive. While this is extremely user friendly and convenient for businesses to have all these applications under one umbrella; it’s also equally convenient for hackers to steal employee/business data. Everything from usernames and passwords to confidential files, all this data is at risk. According to Statista, “…over 879,851 companies in the United States alone use Office 365″. Office 365 isn’t the only office suite application out there, but it is the most popular.
Office 365 has built in protection called ATP (Advanced Threat Protection). Most of our clients have a similar/better service called Mimecast. It is also not perfect. Its job is to filter through and catch scam emails before you ever get a chance to see the messages in your inbox. However, scammers have become more sophisticated in recent years and it’s harder to detect a scam email. According to Clearedin, “97% of people cannot identify a phishing scam.” This isn’t anyone’s fault. Scammers have begun to sound more like they belong to the organization or business they are trying to steal from. This sort of phishing is identified as ‘spear phishing’. Using the tactic of making themselves sound like an admin in the business or another employee will raise the likeliness of you engaging with the email.
So, what are the best prevention practices against Office 365 security breaches?
There are many ways that you can prepare your employees to be on the look out for scam emails. Another statistic from a study by Clearedin showed “an analysis of more than 55 million emails reveals that one in every 99 emails is a phishing attack”. Most common scam emails are just links to landing pages that look very similar to Microsoft logins. Among other attacks are share file attacks, the “action required” attacks, and the voicemail attacks.
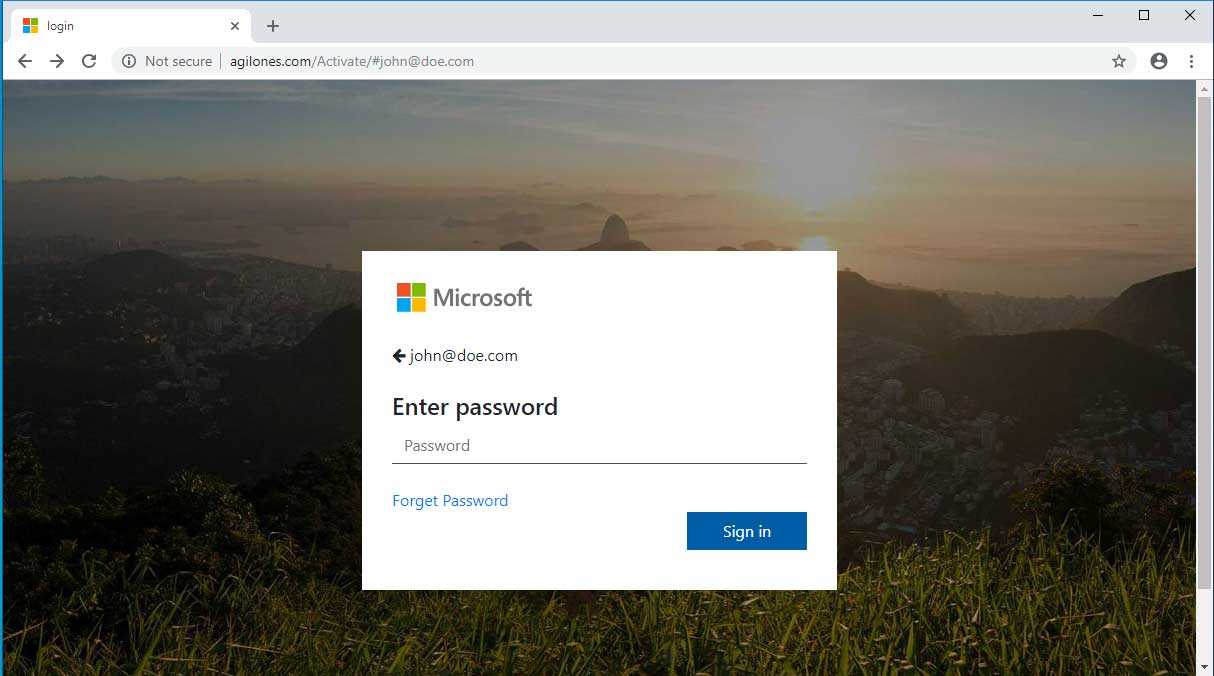
This is an example of what a landing page could look like if you were to click on a scammers email link. The only indication that this isn’t legit is the dangerous URL warning next to the page address.

SharePoint file attacks usually appear as such above and ask you to download a file. These downloads could contain malware that can breach a network.
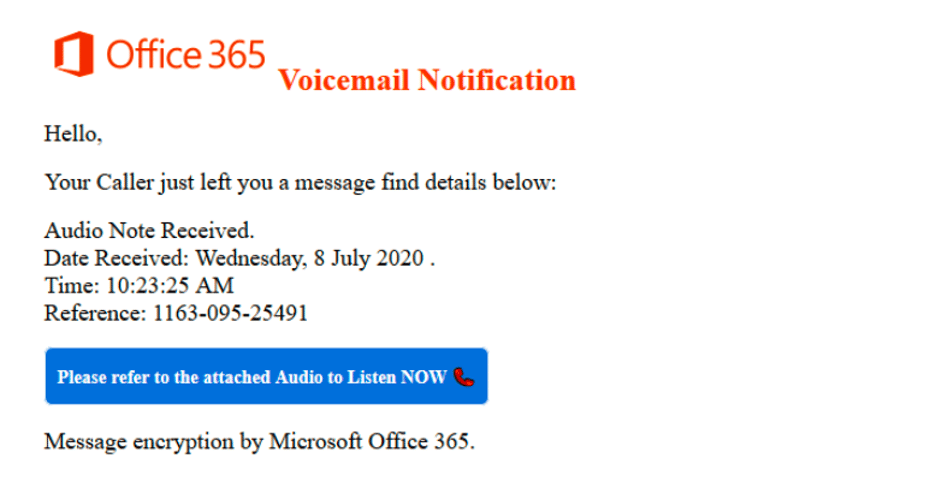
Another example of a phishing email is the “voicemail” attack. These emails typically will provide a link for you to click on that will send you to a landing page asking for your Microsoft username & password information. These emails will have a suspicious sender or have an “external email” message in red at the top of the email.
Anymore, there’s plenty of options for protecting your business/employee data. With Axigent, we are partnered with Mimecast. Mimecast is a security system that specifically protects businesses from email attacks. According to Mimecast, “One threat vector-email-consistently accounts for 90%+ of all new attacks. Moreover, email threats are often the first signal of emerging attacks against other networks and cloud entry points.” Also, a solution to email attacks is to simply implement an awareness training. We recommend any awareness trainings provided by Mimecast, KnowBe4, and Infimia.
Want to know more about us?
Axigent Technologies is based in Amarillo, Texas. We proudly serve the Texas Panhandle, the Dallas/Ft. Worth metro plex and everywhere in between. We partner with businesses to provide consulting and managed IT services!

Follow our social media platforms for announcements and more content!